Warning: Undefined array key 1 in /var/www/wp-content/plugins/monarch/monarch.php on line 4359
by Eliot Leibowitz
It’s tax season. That time of year when Uncle Scam wants to take your money. But it’s not just Uncle Sam we need to be concerned with. Email scams, also known as phishing, are becoming more common as scammers learn new and effective ways to trick people out of their savings. Nowadays, what you don’t know can cost you lots of money. According to the 2017 Norton Cyber Security Insights Report, 143 million consumers in the United States lost 19.4 billion dollars to cybercrime in 2017! You can protect yourself by learning how to recognize and handle phishing emails.
How Do Email Scams Work?
Cybercriminals are con artists. While they are using technology to commit their crimes, they do not exploit technological vulnerabilities as much as human ones. They appeal to human emotion, typically feeding on fear, greed, and/or the human desire to be helpful.
Case in point:
You may have heard of the Nigerian prince scam, probably the oldest scam on the internet. This is known as a funds transfer scam. The email claims that a Nigerian prince, due to war or political unrest, needs to get his money out of the country. He asks for your help in allowing him to transfer funds to your bank account, after which, you will transfer most of the money back to him, keeping a generous sum of a million dollars or so for yourself as a reward for your help. Of course, if you respond, you later hear that due to some complications, an advance fee needs to be paid. If you just pay the $2,000 fee, your million dollars will soon be transferred to you directly. As hard as it may be to believe, people are still falling for this scheme or variations of it today.
Tax Scams
During tax season, the prospect of getting bigger or quicker tax refunds is often used. These emails try to get you to click on a link that looks like it’s going to a legitimate IRS website, like https://irs.gov/refunds. But if you hover your mouse over that link, you’ll see that it actually goes to a malicious website. (Mac users need to have “Show Status Bar” enabled in the Safari view menu to see this.) The words or URL you see on the screen may not be where that link actually takes you. You must move your mouse over the link (without clicking) to see where the link will actually go. That site may look like a legitimate IRS site, asking you to enter private information that can be used to steal your identity, claim your refund, or access your bank account. The link may also download malware to your computer.
Feeding on fear, another email scam threatens to immediately bring in law-enforcement to have the taxpayer arrested for not paying due taxes and demands immediate payment. These emails often use the official IRS logo and include some links to the actual IRS website to make them seem believable. An IRS consumer alert states that:
The IRS will never “demand immediate payment using a specific payment method such as a prepaid debit card, gift card or wire transfer. The IRS does not use these methods for tax payments. Generally, the IRS will first mail a bill to any taxpayer who owes taxes. All tax payments should only be made payable to the U.S. Treasury and checks should never be made payable to third parties.”
How Do I Know If An Email Is A Phishing Attempt?
Start with the golden rule. If it sounds too good to be true, it probably is. You did not inherit $2 Million from a distant cousin. You did not win that lottery you never bought a ticket for (or the one you bought a ticket for but never gave your email address). But also, if it sounds too bad to be true, it probably is. The electric company is not going to turn off your power if you don’t wire money to them in the next hour. Be suspicious of any email you did not expect to receive.
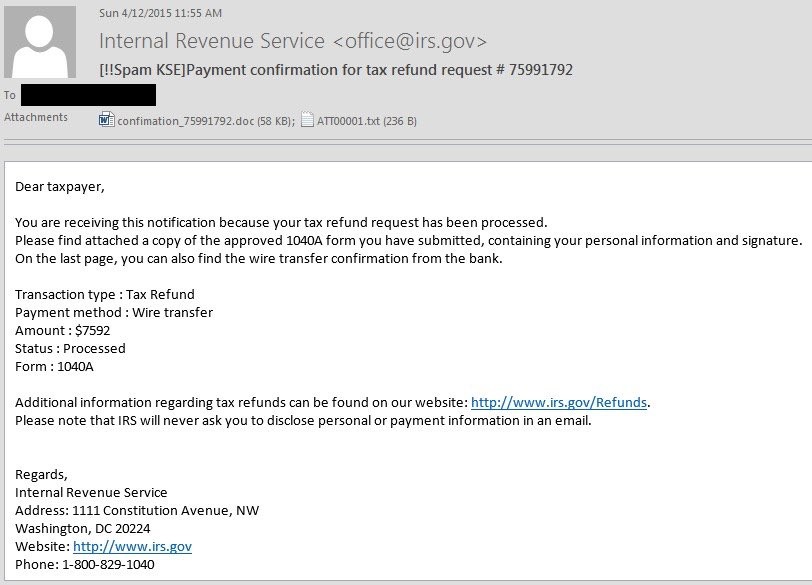
This is an example of an actual phishing email that appears to be from the IRS, irs.gov being the legitimate domain of the IRS. This is a technique known as address spoofing. The attacker uses a tool to mask the sender’s actual address.
Source: KnowBe4
In this case, the system that received this mail was running an email security product that detected it as spam. This is indicated by the “[!!Spam KSE]” added to the beginning of the subject line at the top. Spam is simply unsolicited email that may or may not be malicious. So, people often ignore spam warnings. In this particular email, the links are legitimate, going to the actual IRS website. This adds credibility. So where’s the danger? It is in the attachment. If you open that attachment (located under the blacked out mask), it will launch a ransomware attack, encrypting the files on your computer and demand a ransom to decrypt them so you can regain access to your files.
There are several things in the email that should make you suspicious. The greeting, “Dear taxpayer,” is a red flag. This email is definitely for a specific recipient, so the greeting would certainly include your name. It states that the attachment is your 1040A form. The IRS would have no reason to send this back to you, most certainly not as an attachment. Lastly, the payment method of wire transfer is not how the IRS works.
The right way to handle this or any suspicious email is to go direct to the source, using information you get outside of that email. Do not click on any links or open any attachments. In this example, you can call the IRS to verify the email’s authenticity, but don’t call the number in the email. Look it up on their website or other reliable source.
Spear Phishing
The trickiest email scams are the ones that seem to come from people you know. Gaining unauthorized access to people’s email accounts is a common practice among cybercriminals. There are various methods that cybercriminals use to get access to email accounts. It often starts with a phishing email. They try to trick you into clicking a link that connects to their web server. It may then try to get you to enter your email username and password into a web page that sends it back to them. It may also download a keylogger that records your keystrokes and sends it back to them. The next time you log into your email account they get your username and password from the keylogger.
The lazier cybercriminals may just buy email accounts from the dark web. The dark web is the part of the internet that conventional search engines don’t see. It is a part of the World Wide Web that is only accessible by means of special software, allowing users and website operators to remain anonymous or untraceable. It provides access to websites that carry out illicit activities. You’ve likely heard news reports of data breaches where millions of account credentials (usernames and passwords) had been stolen? That information ends up on the dark web.
If someone gets access to your email account, that gives them access to your contacts’ email addresses, allowing them to email people pretending to be friends or relatives. It also gives them access to a treasure trove of information about you and your contacts. They can use this information in emails to convince you that they are your granddaughter or a friend. After all, who else would know about [fill in secret here]? This type of phishing, directed at you, using specific information about you, is called spear phishing.
Even with emails from your contacts, look for red flags. If it seems odd that your grandson is asking you to transfer money into his account, verify it with him (not in email) before taking any action. If your daughter asks you to download this cool game, talk to her before you click that link.
Signs, Signs, Everywhere A Sign
Here are 8 things to look for that indicate that an email may be suspicious:
- If it sounds too good to be true, it probably is. Yes, I said it again. Live by it!
- The sender’s address does not seem right. An email from Amazon will end in @amazon.com, not @shipping-amazon.com.
- It is asking you for information the sender should already have. Your bank will never ask for your account number or PIN in an email.
- Spelling or grammatical errors. A lot of phishing emails originate from foreign countries and they often make errors.
- That email from your friend or relative doesn’t seem to be something they would send, say, or do.
- It gives a sense of urgency or panic. Sure, some things are urgent, but verify outside of email and don’t use contact information in the email.
- Link text does not reflect the actual destination when you hover your mouse over it.
- The greeting does not include your name.
How Can I Protect Myself?
Now that you know how to spot a phishing email, how do you protect yourself?
Think before you click that link. Remember that you can hover over the link to see where it really goes. It’s worth noting that even security experts sometimes get fooled. So, it’s good to take steps to protect yourself if you do click a bad link. Here are 3 steps you can then take:
- Disconnect from the internet.
- Clear the cache in your web browser.
- Scan for malware. If you don’t know how to do this and you have Chrome installed, you can enter chrome://settings/cleanup in the address field (where you enter the URL of a website) and clicking the Find button.
There are free security tools available to warn you about malicious websites if you try to access them. Some also scan any files you download to block malware. They are not perfect and sometimes will allow a bad site through or block a good site, but overall, it’s worth the added security. If you don’t have one running yet, give McAfee WebAdvisor a try.
Make sure you’re running the security apps on your computer. They all come with some form of antivirus and other protection. Check out the security settings for whichever system you use. Macs have good security protection built in but you can still check and adjust the security settings. Windows users that are using the malware tool included with Windows can use Windows Defender Offline.
Your personal information is valuable. Protect it as though it is cash. Never provide personal information via email. A reputable company would not ask you to do so.
Protect your email account with a strong password and multifactor authentication that is not used for any other account. Your email account holds the keys to your digital kingdom. Providing the proper level of protection can save us from losing our money.
About The Author
Having retired from his role as Security Practice Head for a global telecom company, Eliot Leibowitz is now leveraging his 30+ years of providing security expertise to Fortune 500 companies to write about cybersecurity, technology, and anything that grabs his interest. He is currently working on a couple of projects to make the online world a safer place. The Cybersecurity Awareness Project is a work in progress helping organizations with information on how to plan, build, and run security awareness programs for their employees. Simply Safe Online, still in its embryonic phase, will be a free resource to anyone interested in simple steps to stay safe online.
I’m a self-professed madman, adventurer, photographer, certified High-Performance Coach, martial artist, and licensed physical trainer specializing in senior fitness. My passion is to continue growing and developing into my own unique, gifted, and joyful authenticity, while committing myself towards doing my own special part to help change the world. My mission is to help others find their own direction and purpose in life, by means of mentoring, teaching, and empowering.